New to deploying OCI GoldenGate and unsure about networking? No worries, this guide will walk you through some key points:
- Private Subnet: OCI GoldenGate currently requires a private subnet for deployment. This ensures security by keeping your resources within a dedicated network segment.
- IP Addresses: Each source and target connection in your GoldenGate deployment will need an IP address. These addresses allow communication between GoldenGate instances and your resources.
While this covers the network foundation, there’s more to explore! Consider these resources to delve deeper:
https://docs.oracle.com/en-us/iaas/Content/Network/Concepts/dns.htm#Private_view
https://docs.oracle.com/en/cloud/paas/goldengate-service/oootq/#articletitle
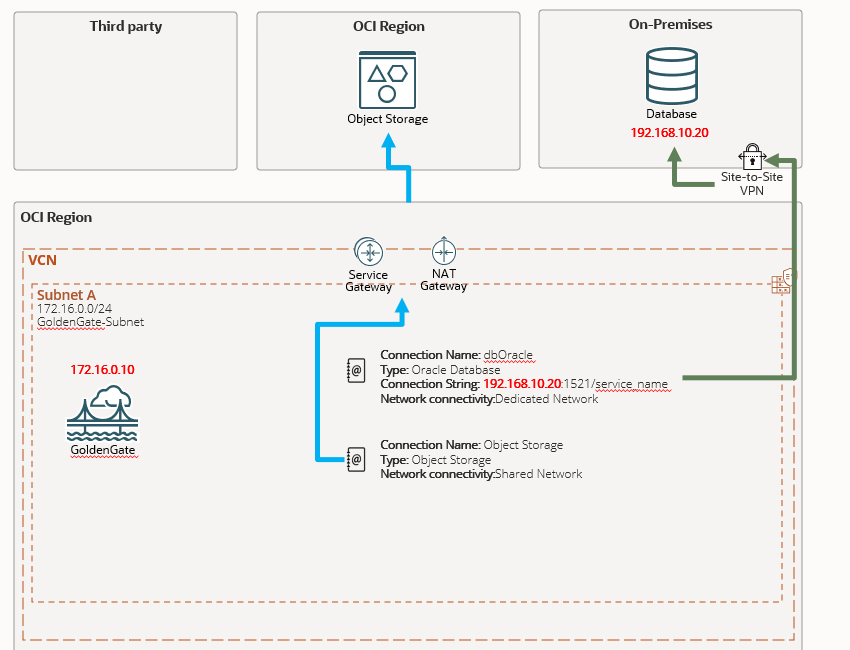
Planning the subnet
- Create a Private Subnet:
- Begin by creating a private subnet within your chosen Virtual Cloud Network (VCN). This subnet will host your GoldenGate deployment, ensuring secure isolation from the public internet.
- Configure a NAT Gateway:
- The NAT Gateway acts as an intermediary, allowing instances within your private subnet to connect to external resources with a public IP address.
- Route table:
- Modify the route table associated with your private subnet. Ensure all outbound traffic destined for the internet is routed through the NAT Gateway (if configured). This ensures controlled access while maintaining secure communication.
- Configure DNS Resolution (Optional but Recommended):
- Although not strictly necessary, setting up DNS resolution within your VCN will simplify managing and connecting to your resources. You can configure a private DNS zone or leverage Oracle Cloud Infrastructure DNS. This allows you to access your resources using a user-friendly hostname instead of its IP address.
The basic
To start, you need to know how could you reach your source/target, depending on the location and accessibility of your resource, you can choose various connectivity methods.
If your source/target resides on-prem, establish a secure connection between your on-prem network and OCI using a VPN or FastConnect, configure your route table to direct traffic to the appropriate endpoint, don’t forget to implement security lists on your subnet to control inbound and outbound traffic, ensuring only authorized access.
Once you understand the network setup, configuring connections within the OCI GoldenGate console generally follows a consistent process. Specific details might vary based on the connection type you choose.
For Oracle connections, you need to know the IP adress, listener port and service name, you can use the Easy Connect method: DB_IP:PORT/SERVICE , and of course the username and password, but here we are focusing in the network side.
Endpoint Selection:
OCI GoldenGate offers two primary endpoint modes to connect to your source/target databases:
Shared Endpoint: If your source/target has a public endpoint, the connection will originate from the Deployment IP.
Dedicated Endpoint (For Private Networks): Choose this mode if your source/target resides within a private network. Select a subnet with connectivity to your source/target, and the connection will originate from the dedicated IP assigned to that endpoint.
Regardless of the chosen endpoint mode, you can leverage Security Lists/NSGs to further restrict traffic and enforce security policies.
The intermediary
Currently, OCI GoldenGate deployments are restricted to private subnets. This enforces security by isolating your GoldenGate instance from the public internet, if you have multiple GoldenGate deployments, you need to create separate GoldenGate type connections and assign them to each deployment, you don’t need to specify an user and password because it is stored inside the GoldenGate Credential Store.
Create a connection and choose the Dedicated Endpoint option and specify your subnet, don’t forget to edit the security list and route table if needed.
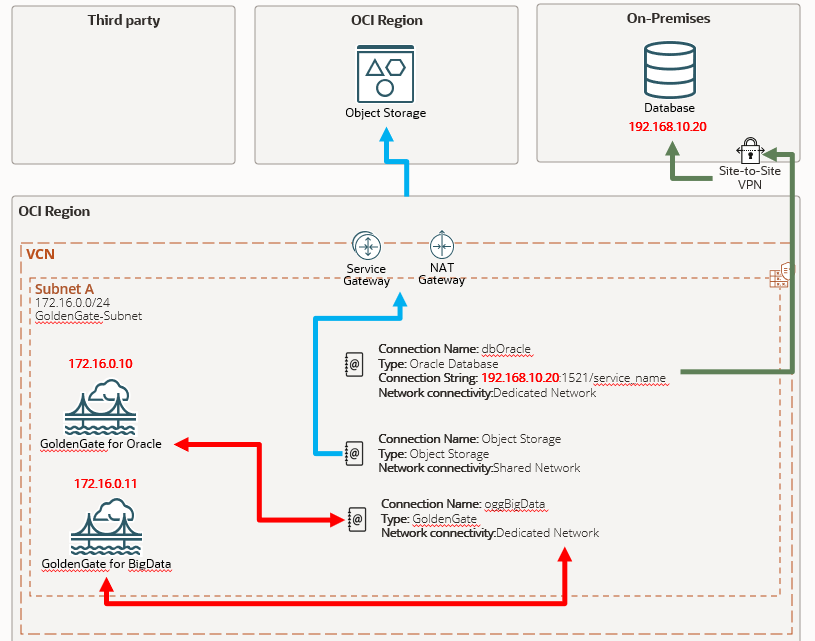
If you don’t create and assign the connection, your distribution path will throw an error like this:
The network connection could not be established: OGG-10390 - Generic error -1 noticed for endpoint wss://xxxx.deployment.goldengate.REGION.oci.oraclecloud.com:443/services/v2/targets?trail=xxxx. Error description - Host not foundNot so advanced
While not mandatory for basic functionality, configuring DNS resolution within your Virtual Cloud Network (VCN) offers several benefits, by creating/updating a private DNS zone within OCI, you gain centralized control over your DNS records. This simplifies updates and ensures consistency across your environment.

Within your private DNS zone, create records for your source and target databases. Each record will have a name (e.g., mydb) that will be appended to your zone name.
In the provided example, mydb.conexoes.goldengate points to a private IP address, instead of using an IP address, you can create your OCI GoldenGate connection using the DNS hostname: mydb.conexoes.goldengate:1521/service
If you need to modify the database’s IP address in the future, you only need to update the DNS entry, eliminating the need to recreate the connection in OCI, DNS integration often automates this process in real-world environments, ensuring consistency between OCI and your on-premises (ONP) network.
Other important thing is when you have a RAC database, this connection type will use two IPs from your subnet and you need to choose Redirect Mode in the connection screen.
If you have a very specific requirement that is not covered by any available connection, you can have a Generic type connection and enter the informations.
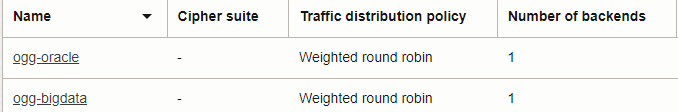
For public access you can choose the option “Enable Public Access” while deploying and it will create a Load Balancer with required resources(NSG, sec list, etc) but if you have more than one deployment maybe you will prefer to have just one LB and control it, so create your GoldenGate instances, create one Load Balancer with multiple backend set, each one point to one deployment and assign a different ingress port.
Backend Sets:
Your backend needs to point to GoldenGate instance private IP in TCP port 443:
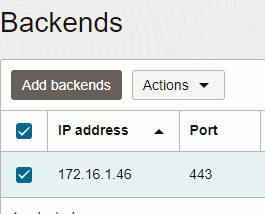
And you can configure your Listner in different ports:
While this guide covers common scenarios, GoldenGate offers various configuration options. If you encounter unique requirements, I’m happy to discuss further